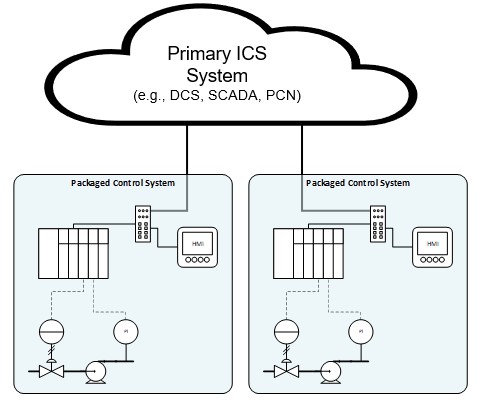
Packaged control systems (PCS) are a mainstay in industrial environments due to their standardized functionality, ease of integration, cost efficiency, and rapid deployment. From gas compression skids to boiler control systems and vapor recovery units, PCS offer a pre-engineered, plug-and-play approach that enables organizations to quickly meet operational needs. However, these benefits come at a significant cost because they are often the most overlooked and vulnerable components in Operational Technology (OT) cybersecurity programs.
What are Packaged Control Systems?
Packaged control systems are modular units designed to monitor and control specific industrial processes or equipment. Delivered by original equipment manufacturers (OEMs) or system integrators (SIs), PCS can be standalone or integrated into larger control architectures such as Distributed Control Systems (DCS) or SCADA platforms. Their standardized design and rapid deployment make them attractive for both new (greenfield) and existing (brownfield) facilities. Their modularity and pre-engineered nature allow for quick installation and integration, but this convenience comes at a cost, especially when it comes to cybersecurity.
Why are PCS So Challenging to Secure?
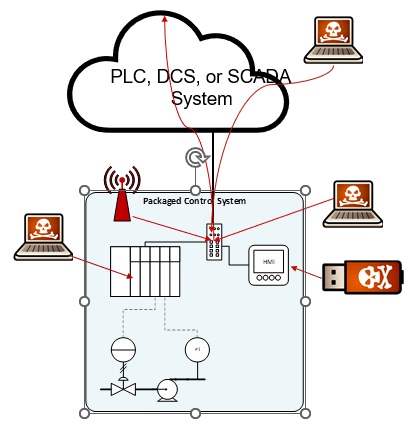 Despite their operational benefits, PCS often introduce significant cybersecurity risks into OT environments. Several factors contribute to this challenge:
Despite their operational benefits, PCS often introduce significant cybersecurity risks into OT environments. Several factors contribute to this challenge:
- Lack of Built-In Security: Many PCS are designed for functionality and speed, not security. They frequently lack intrusion detection, encryption, and robust access controls.
- Limited Patch Management: PCS may not be regularly updated or patched, leaving them exposed to known vulnerabilities.
- Integration Challenges: PCS are often connected to legacy systems and broader ICS networks, amplifying risk through insecure protocols and outdated hardware.
- Remote Access and Visibility Issues: OEMs or SIs may maintain remote access for support, sometimes without proper oversight, increasing the attack surface.
- Unmanaged Network Devices: PCS commonly use unmanaged switches and lack boundary devices like firewalls at the network edge.
The Open Industrial Protocol Dilemma
Open industrial protocols—such as Modbus, OPC DA, Ethernet/IP, DNP3, and PROFINET—enable interoperability and vendor independence in industrial environments. However, many of these protocols were designed before cybersecurity was a major concern. Modbus, for example, is a clear text protocol that requires no authentication, making it highly vulnerable to interception and manipulation, yet it remains the most popular protocol for integrating PCS with other control systems.
The widespread use of unsecure protocols in PCS, especially when connected to larger networks, exposes facilities to significant risk. Attackers can exploit these vulnerabilities to disrupt operations, damage equipment, or even take control of critical processes.
Consequences of Compromise
A successful cyber-attack on a PCS can have cascading effects:
- Health and safety risks
- Environmental damage
- Equipment failure
- Production shutdowns
- Off spec or unsafe products
- Financial losses and reputational harm
Strategies for Securing PCS
For Existing (Brownfield) Systems:
- Cyber Design Review: Assess system architecture, asset inventory, and policies.
- Cyber Risk Assessment: Conduct consequence-based cyber risk assessments following methodology that is aligned with the ISA/IEC 62443-3-2 standard. The CyberBowtie methodology is an excellent choice because it is efficient and intuitive.
- Remediation: Implement changes, test, and update documentation.
- Continuous Monitoring: Use intrusion detection and SIEM tools to monitor for suspicious activity.
For New (Greenfield) Systems:
- Cybersecurity Requirements Specification (CRS): Define and communicate security requirements to OEMs and SIs during procurement.
- Cyber Risk Assessment: Conduct cyber design reviews and 62443-3-2 compliant risk assessments throughout the engineering and commissioning phases.
- Cybersecurity Integration Plan (CIP): Create a concise plan for securely integrating the new system into the plant network, covering essentials like patching, backups, and incident response.
- Cyber FAT and SAT: Perform cyber factory and site acceptance testing to verify security controls in both test and production environments.
- Operational Security: Establish operating procedures for maintaining security, including regular updates and continuous monitoring.
The Path Forward
Securing packaged control systems may seem challenging at first, but it’s not too difficult if you follow the practical guidance outlined in this blog. Start by setting clear requirements, conducting risk assessments, and thoroughly testing your systems. These steps will help you tackle the most common vulnerabilities and make your packaged control systems much more resilient to cyber threats.
The key is to be proactive: engage suppliers early, specify your cybersecurity needs, and make security a routine part of system integration and ongoing operations. With the right planning and commitment, organizations can confidently protect their PCS, minimize risk, and maximize operational reliability. Remember, cybersecurity doesn’t have to be overwhelming. Success comes from consistency and attention to detail.