by Josh Ruff & Luis Sanchez
Industrial enterprises now find themselves at the nexus of two traditionally distinct domains: information technology (IT) and operational technology (OT), as cyber threats become more complex and widespread. Despite recent advancements in the integration of IT and OT environments, the corresponding security models have not evolved at the same rate. Organizations take several approaches to OT security. Some delegate tasks to centralized IT cybersecurity teams, while others include cybersecurity responsibilities into Automation or OT infrastructure roles. Initiating any security efforts is generally seen as beneficial, but for larger organizations aiming for maturity, a hybrid collaboration between IT and OT teams may be effective, particularly regarding cybersecurity. IT staff often possess knowledge of current cybersecurity technologies and developments, while OT staff typically have expertise in OT-specific technology and operational contexts.
With that in mind, addressing the seemingly monumental task of maturing your OT security monitoring capabilities involves several key considerations. Should you integrate OT telemetry into your existing IT SOC, establish a separate OT SOC, or approach it with a hybrid SOC mentality? What telemetry should be ingested? Are traditional IT SOC use cases adequate for an OT environment?
Perhaps you’ve started integrating some telemetry into your IT SOC but haven’t yet seen the full benefits. It may be time to consider moving beyond the idea of “convergence” and toward a truly consolidated or integrated SOC model; one that is purpose-built to handle the unique demands of both IT and OT environments.
The Problem with Traditional SOC Models
Most SOCs today are designed with a traditional IT mindset. They excel at monitoring enterprise infrastructure, endpoints, applications, and cloud environments, but when it comes to monitoring Industrial Control Systems (ICS), Distributed Control Systems (DCS), PLCs, and SCADA platforms (to name a few) they usually don’t know where to start. A SOC staffed with IT personnel and an IT mindset will not be sufficient to properly monitor OT systems. Here’s why:
- Blind Spots in OT Telemetry: Traditional SOCs may pull in data from OT environments, but they often focus on IT-adjacent assets like servers or network switches. Critical OT telemetry, such as alerts from or logs from specialized OT applications and OT specific security monitoring solutions, is either ignored or misunderstood.
- Lack of OT Context: Even when OT data is ingested, IT analysts typically lack the domain knowledge to interpret it. For example, an engineering workstation connecting to or going online with a PLC to make minor changes might be flagged as suspicious in an IT context but could be part of a scheduled maintenance window in OT.
- Lack of OT-Aware Detection and Response: IT SOC analyst staff do not have the background and insight to develop OT-specific playbooks and respond appropriately to alerts like unauthorized firmware downloads or abnormal SCADA commands; events that would be meaningless or misinterpreted in a traditional IT SOC.
Bridging the IT/OT Security Gap
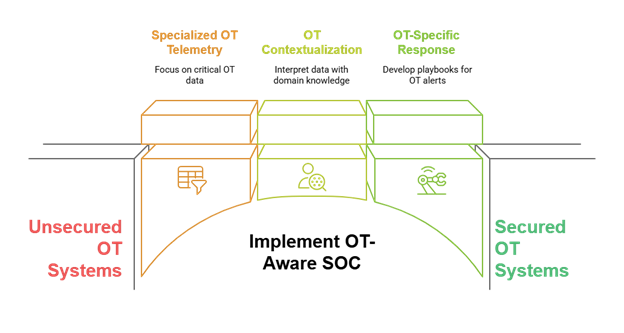
However, this does not mean that you shouldn’t consider leveraging your traditional SOC dashboards, playbooks, and solutions for the like in kind assets in OT (you should, as IT has excelled at this for some time). On the contrary, you should leverage your IT SOC knowledge while understanding that OT comes with its own set of problems, proprietary protocols, data sources, and use cases that need to be developed to properly monitor an OT ecosystem.
Why Consolidation Matters Now More Than Ever
As OT environments grow and become more integrated with IT and cloud systems, the complexity and attack surface expands. Threat actors can now move laterally across domains, exploiting gaps in visibility and response. A consolidated SOC staffed with a team that has both IT and OT skillsets addresses this by:
- Providing Centralized Visibility: A single pane of glass across IT and OT enables faster detection of cross-domain threats and reduces the time to triage and respond.
- Fragmented Incident Response: Separate SOCs for IT and OT create coordination challenges during incidents. Analysts must manually piece together attack paths across environments, slowing response times and increasing the risk of oversight.
- Operational Inefficiencies: Maintaining two separate SOCs increases overhead with duplicated tooling, staffing, and processes without delivering unified visibility or faster resolution.
- Reducing Costs and Complexity: Consolidation eliminates redundant processes and tools, streamlining operations, and lowering the total cost of ownership.
But What About the Case for Separation?
While there is a great argument for having a consolidated SOC across both domains, there are still valid reasons why some organizations would want to or even need to maintain separate SOCs:
- Operational Isolation: Sometimes OT must be separated from IT for safety, compliance, or to prevent threats from spreading if IT is breached. A separate OT SOC can maintain visibility even when isolated.
- Tailored Operating Models: OT environments often require different Service Level Agreements (SLAs), escalation paths, and tooling. Separate SOCs allow for more flexibility in how each domain is managed.
However, maintaining multiple SOCs will inevitably have its drawbacks, so the benefits must be weighed against the growing need for unified threat detection and response. In many cases, a hybrid model where IT and OT teams operate within a shared SOC but retain domain-specific workflows can offer the best of both worlds.
Building vs. Buying: The SOC Dilemma
Standing up an internal, consolidated SOC is a big task that will take careful planning. It requires:
- Specialized Talent: Most SOC teams are staffed with IT professionals. Finding analysts with OT expertise or training among the existing staff can be a major challenge.
- Custom Playbooks: OT alerts require different logic and response paths. For example, repeated firmware downloads from an engineering workstation might be normal or a sign of compromise, depending on how the organization operates. Playbooks must reflect these nuances.
- 24/7 Coverage: Industrial environments don’t sleep, and neither should your SOC. Around-the-clock monitoring is essential for both the safety and security of any organization ready to invest in SOC monitoring for OT.
Weighting SOC Options for OT Security

Given these challenges, organizations are turning to Managed Security Service Providers (MSSPs) with deep OT expertise to close their OT monitoring gaps. MSSPs can provide rapid coverage, mature processes, and access to specialized tools without the overhead of building a SOC from scratch.
That being said, if an organization is large and mature enough, it can make a lot more sense to integrate their OT monitoring telemetry into an existing IT SOC or build out and properly staff their own consolidated SOC. Once you’ve made your initial investment in building out your SOC, you own it and can tailor it to your specific needs.
A Blueprint for Success: Integrated Partnerships
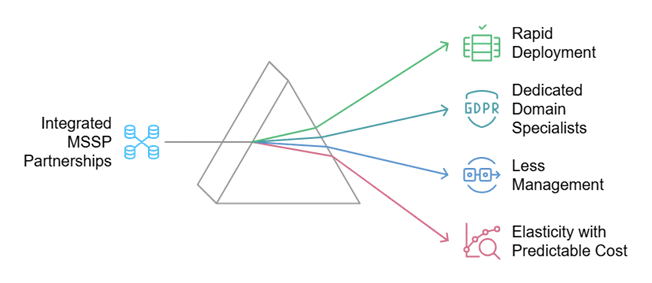
In a case where an organization wants to move forward with having a consolidated SOC monitoring and response capability and wants to be more hands-off, it may be worth considering partnering with multiple MSSPs (IT and OT service providers respectively) who are willing to integrate both environments into the same SOC environment. In a perfect world, these MSSPs would already have a partnership or SOC analysts proficient in both domains to provide a unified environment with the appropriate prerequisite skill sets. The benefits of leveraging an MSSP would be:
- Rapid Deployment: Rather than spending years and major resources building an in-house SOC, organizations can quickly utilize an established SOC team, proven models, templates, playbooks, and potentially achieve SOC II compliance much faster.
- Dedicated Domain Specialists: Domain specialists with years of experience in deep protocol visibility, proactive threat hunting, and incident response tailored for industrial and business environments.
- Less Management: MSSPs handle hardware, software, and staffing, allowing organizations to concentrate on their core operations.
- Elasticity with Predictable Cost: Organizations can scale their monitoring operations up or down as needed, with pricing models that are directly linked to the services. This enables more accurate budgeting for security monitoring activities.
Unveiling the Benefits of Integrated MSSP Partnerships
Ultimately, an organization should assess which cybersecurity monitoring model aligns best with its goals, objectives, and operational constraints. MSSP models may have certain limitations, as they are generally less flexible in customizing their solutions to specific organizational needs.
It’s time to approach IT and OT with a unified mindset, aligning day-to-day security objectives through shared tactical goals and coordinated tasks. True cybersecurity maturity happens when these two functions operate not in silos, but in sync, where organizational cultures and objectives mix into a seamless flow. This confluence of security is what drives continuous improvement across both IT and OT environments, technically and culturally.
As demand for data analytics and enhancing productivity and flexibility grows, IT and OT domains are becoming more interconnected. Organizations are increasingly using IT technologies like cloud computing and AI to improve operational efficiency, leading to more integrated operating models. Since operational and regulatory requirements vary by industry, it’s important to carefully assess your needs and options when choosing SOC monitoring solutions.
The advancement of industrial cybersecurity monitoring is centered on achieving effective cross-domain integration where feasible. Establishing a unified SOC represents more than a technical enhancement; it constitutes a strategic necessity for closely connected operational domains. In today’s increasingly interconnected environment, such an approach provides comprehensive visibility, rapid response capabilities, and enhanced resilience essential for safeguarding both digital and physical assets.



