Armexa’s cybersecurity experts bring decades of operational experience and were instrumental in shaping the internationally recognized International Society of Automation/International Electrotechnical Commission (ISA/IEC) 62443-3-2 standard for security risk assessment in system design. Our consequence-based risk assessment methodologies are grounded in that ISA/IEC 62443-3-2 standard, ensuring a structured and standards-based approach to OT risk analysis. Armexa offers two options: CyberHAZOP™ and CyberBowtie™.
The choice between these methodologies typically depend on the preferences of the client’s stake holders, aligning with their established practices for risk analysis and communication.
Solutions
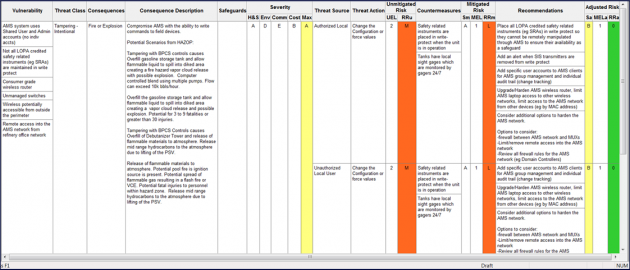
OT CyberHAZOP™
OT CyberHAZOP, also known as CyberPHA, is a proven, safety-oriented, systematic method to study OT cyber risks. It is based on hazard and operability studies (HAZOP) studies that are used widely in process safety management, particularly in industries that operate highly hazardous industrial processes (e.g. oil and gas, chemical, etc.).
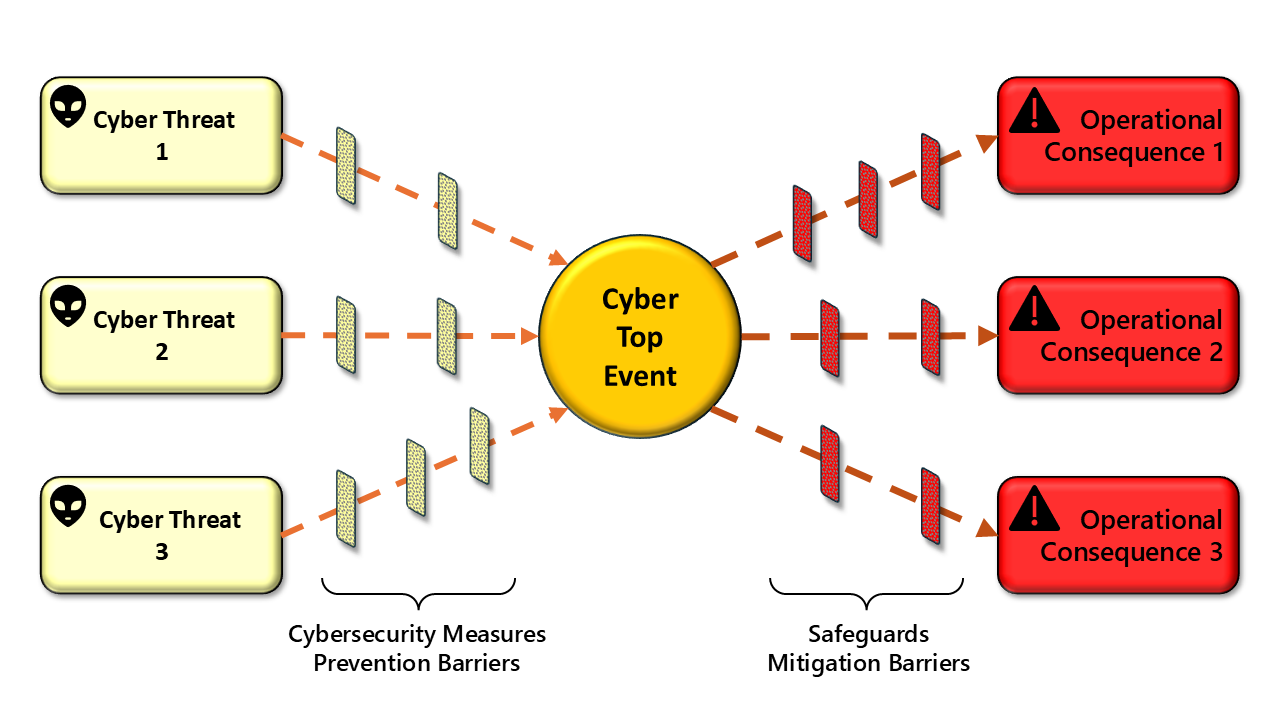
OT CyberBowtie™
OT CyberBowtie is a graphical risk analysis approach that maps cyber threats to events and operational consequences, depicting the barriers that either prevent the event or mitigate the consequences —enabling consequence-driven decision making and clear communication of findings. It intuitively identifies and ranks cyber risks in your OT environment.
What is OT Cyber Risk?
The term “risk” is often used interchangeably with vulnerabilities or gaps—but they aren’t the same thing. Simply put, OT cyber risk is the potential for disruption or harm to industrial systems due to cyber threats. In the context of OT cybersecurity risk assessments, risk emerges when a threat exploits a vulnerability, resulting in a consequence to your operations.
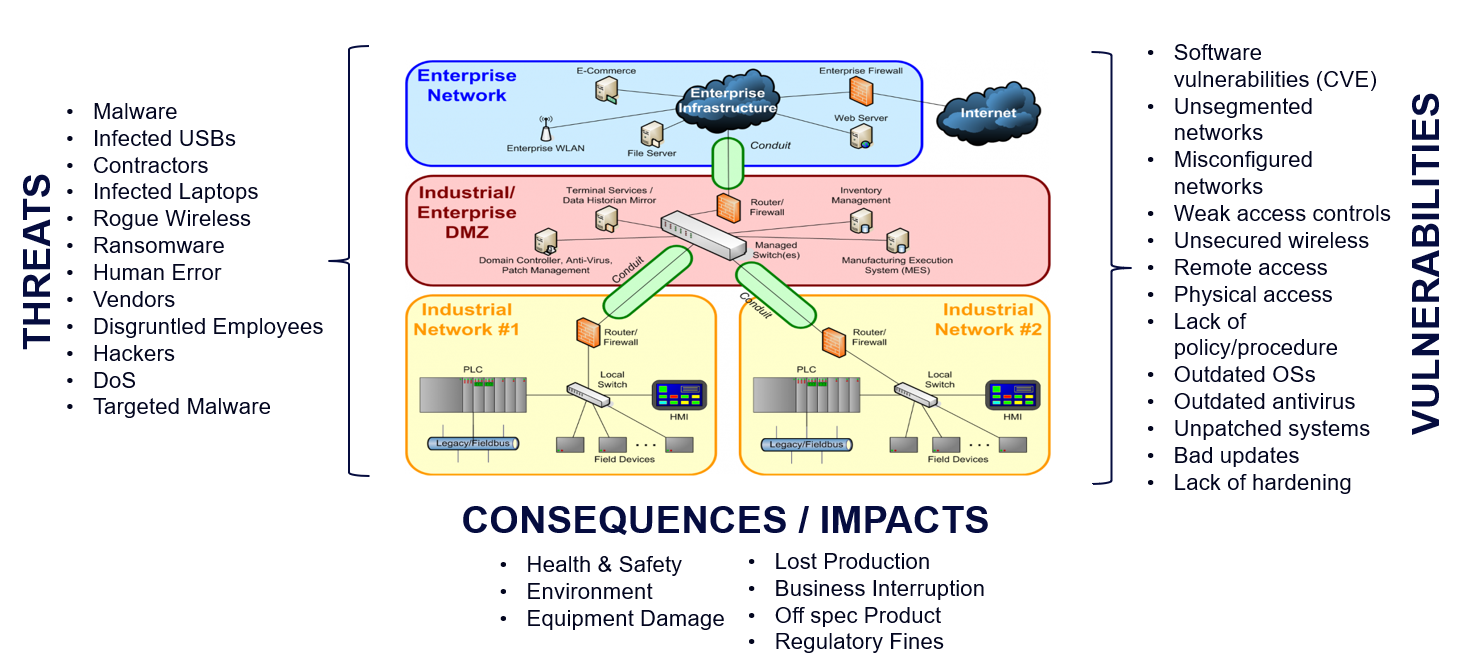
When we look at risk, its generally these three components:
- Threats are ongoing and often beyond your direct control. They include things like malware-infected USB drives, infected contractor laptops, rogue wireless access points, and ransomware.
- Vulnerabilities exist in every system—no environment is perfect. These might include known software flaws (CVEs), poor network segmentation, misconfigurations, weak access controls, or unsecured remote access.
- Consequences can range from production loss and business interruption to environmental damage, equipment failure, or even health and safety incidents.
Why Armexa?
We don’t just follow the standards—we helped write them. Our team has led hundreds of consequence-based assessments across critical infrastructure sectors. With deep expertise in both cybersecurity and process safety, we deliver insights that are practical, defensible, and immediately useful.
Hear from the experts on our consequence-based methodologies.
Part of Armexa's 3D Assessments
Armexa’s 3D assessment model is a systematic, three-dimensional approach designed to provide a holistic view of an organization’s OT (Operational Technology) cybersecurity posture. Each dimension, or element, provides a distinct but interdependent perspective on the cybersecurity of a facility or system.
Maturity/Compliance Gap Assessment: This evaluates how well an organization’s cybersecurity practices align with industry standards like NIST CSF and ISA/IEC 62443. It informs leadership about their current security posture relative to peers and regulatory expectations Learn More
Validated System Design Review: This involves a deep technical analysis of system architecture, network segmentation, data flow, and endpoint configurations. It helps uncover vulnerabilities in the actual implementation—not just theoretical gaps. Learn More
Consequence-Based Risk Assessment: This is where Armexa stands out. Using CyberHAZOP and CyberBowtie methodologies, it identifies the most critical operational risks and recommends the most cost-effective mitigations. This approach prioritizes real-world impact over theoretical vulnerabilities.