𖠿 > Services > Risk Management > Consequence-based > OT CyberHAZOP
A Cyber Hazard and Operability Analysis (CyberHAZOP), also known as a CyberPHA, is a consequence-based, safety-first approach to conduct a security risk assessment for OT systems, as required by many industry standards.
Similar to a traditional HAZOP safety engineering study but adapted to assess the potential consequences of cyber threats and identify measures to mitigate unacceptable risks. The CyberHAZOP methodology is widely accepted by OT functional disciplines due to their familiarity with conventional HAZOP safety studies.
Corporate and facility managers often struggle with how to best allocate limited resources to achieve their security goals. CyberHAZOP can serve as a strategic tool to ensure maximum risk reduction per dollar spent. While plant personnel may recognize the importance of OT cybersecurity risks, they often face challenges in building a compelling business case to justify the necessary investments to management.
The methodology has been applied hundreds of times by companies in a variety of industries, especially in regulated critical infrastructure sectors. It is used in a wide range of OT environments, including:
- Industrial control systems (ICS)
- Safety instrumented systems (SIS)
- Industrial IoT systems (IIoT)
- Building Automated systems

Our Approach
Armexa’s CyberHAZOP/Cyber PHA process offers a systematic approach aligned with ISA/IEC 62443‑3‑2, Security Risk Assessment for Design, and integrates guidance from NIST CSF and NIST SP 800‑82 where applicable. By leveraging the expertise of safety engineers, operations, IT, and OT security professionals, the process ensures that risk decisions reflect operational reality. Conducting a CyberHAZOP assessment collaboratively provides a clear picture of realistic threats that could compromise your system and lead to significant operational consequences, including impacts to health, safety, the environment, or major production losses.
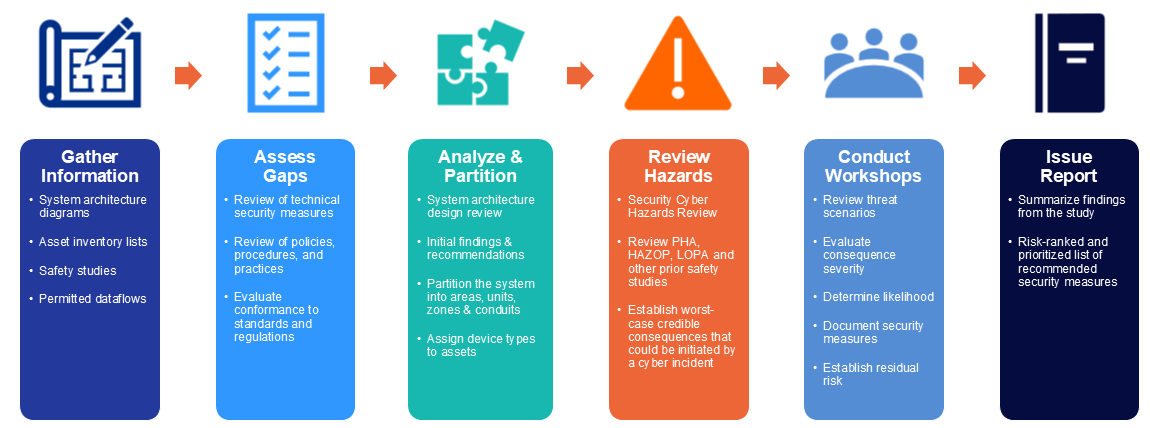
Results and Benefits
Risk Identification and Ranking
CyberHAZOPs/CyberPHAs systematically identify critical assets, known vulnerabilities, and potential threat scenarios.
- Each threat scenario is evaluated using a risk matrix to determine its severity and likelihood.
- Consequence-driven analysis to map out how cyber incidents could lead to hazardous outcomes
Prioritized Recommendations and Mitigation Planning
- The result is a prioritized list of recommended security controls and mitigation strategies
- A project specific roadmap is created to balance the study recommendations against available resources and operational constraints.
Integration with Safety Studies
- CyberHAZOPs leverage data from existing safety assessments, when available, like HAZOP and LOPA (Layer of Protection Analysis) to ensure alignment between safety and cybersecurity disciplines
Operational Improvements
- Studies such as CyberHAZOP facilitates better alignment among internal organizations (e.g. IT, OT, HSE) that may not typically interact
- CyberHAZOP findings uplift organizations to better incorporate cybersecurity into facility design and operation, improving resilience and compliance from the ground up
Training and Awareness
- CyberHAZOP generally increase awareness and serve as on-the-job training for participants.
- The process often leads to enhanced training programs and awareness campaigns for OT personnel, ensuring that cybersecurity becomes part of the operational culture
Case Study

OT Cybersecurity Risk Assessments for a World Class Renewable Energy and Green Hydrogen Facility
The client selected us to lead these assessments, an ambitious critical undertaking given the facility’s scale and global engineering footprint, based on our proven track record of conducting cyber HAZOP assessments per the international standard, ISA/IEC 62443-3-2. These assessments ensured that cybersecurity was embedded into the plant’s foundational design, by identifying, ranking, and addressing risks across interconnected systems and ensuring alignment with regional regulations and international standards.
Armexa’s Consequence-Based Risk Assessment solutions identify the most critical operational risks within an industrial environment and prioritizes cost-effective mitigation strategies tailored to those risks.



