𖠿 > Services > Risk Management > Consequence-based > OT CyberBowtie™
The Armexa OT CyberBowtie™ Risk Assessment methodology is based on the ISA/IEC 62443 standard, “Security for industrial automation and control systems – Part 3-2: Security risk assessment for system design”. Our solution helps you identify, visualize, and mitigate cybersecurity risks across your OT environment. Adapted from proven process safety frameworks, our methodology provides a clear, consequence-based view of how cyber threats can lead to operational disruptions and what safeguards and/or security measures are in place or are needed to prevent them.
Traditional assessments often stop at policy reviews and compliance checklists. Our OT CyberBowtie approach goes further—mapping threats, vulnerabilities, and consequences in a single, intuitive model. Whether it’s ransomware, misconfigurations, or insider threats, our workshops help you pinpoint weak spots and prioritize the controls that matter most, ensuring your spending is targeted towards where it will have the greatest impact.
Our Approach
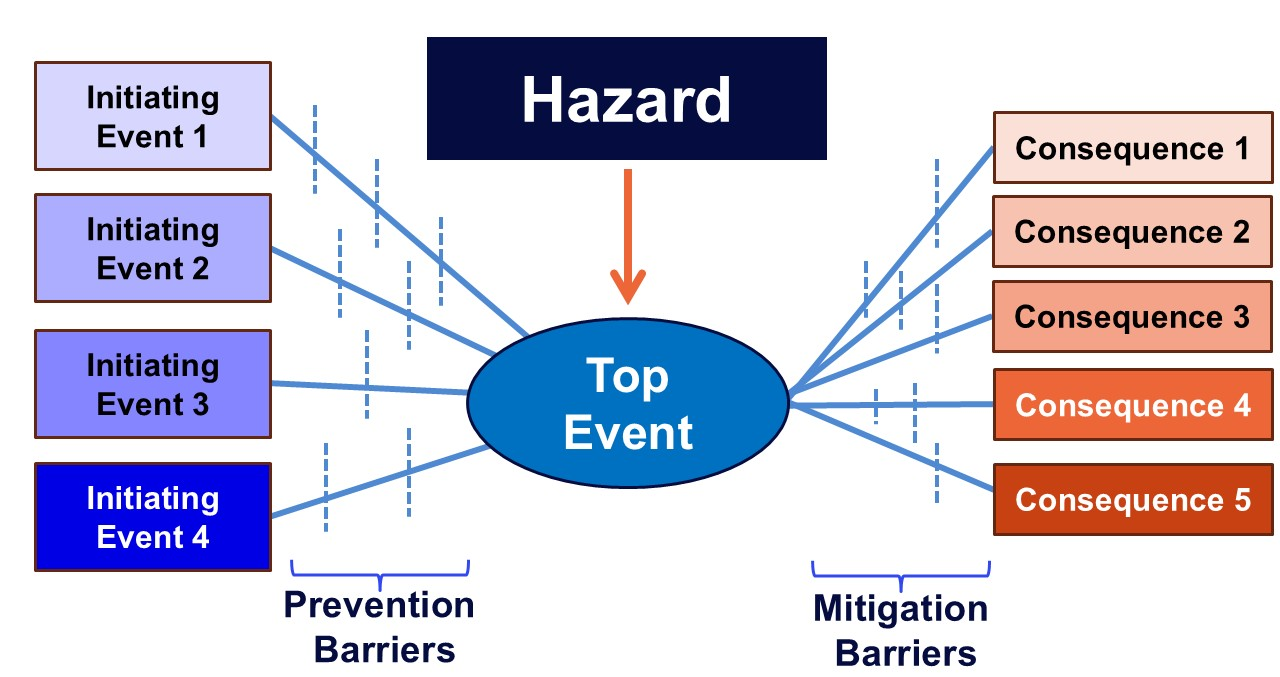
The Armexa OT CyberBowtie risk assessment methodology uniquely integrates security with reliability and safety requirements using a common risk management approach and provides management with the information needed to evaluate and prioritize cybersecurity investments. Each engagement begins with a review of your OT architecture, partitioning of the system into zones and conduits, and the definition of “top events”—such as loss of control or loss of view. We then build a custom Bowtie diagrams for your application with your team that:
- Lists cyber threats (initiating events) on the left that could lead to the Top Event (e.g., unauthorized access, malware)
- Identifies operational consequences (e.g., safety incidents, environmental harm) on the right that could result from the Top Event
- Illustrates barriers that could prevent or mitigate the top event
- Barriers are assigned an effectiveness score for strength and reliability, enabling a clear view of where your defenses are strong—and where they need reinforcement.
- The risk of each modelled threat-consequence pair is determined and documented.
Unlike typical a gap assessment, our CyberBowtie sessions are dynamic and collaborative. We bring together IT, OT, and operations personnel in real-time workshops that make risk visible and actionable. This hands-on approach accelerates the identification of weak or missing barriers and high-value opportunities for risk reduction. By contributing their insights and expertise, team members gain a stronger sense of ownership and buy-in, which drives more effective implementation and sustained commitment to risk management strategies.
The end result of the process is a completed CyberBowtie diagram, prioritized recommendations, and a roadmap outlining a practical sequence of tasks for mitigating unacceptable risk. The CyberBowtie graphical and straight forward presentation makes it easy to communicate to non-experts and senior leadership.
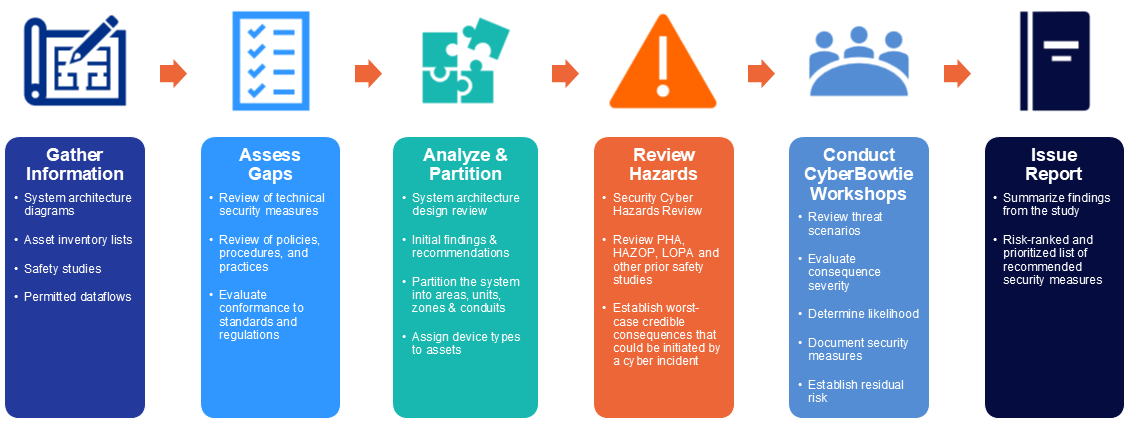
Assessment Phases
Results and Benefits
The OT CyberBowtie Risk Assessment provides a comprehensive, visual, and actionable approach to managing cybersecurity risks in operational technology environments. The assessment emphasizes real-world relevance by focusing on operational consequences rather than abstract compliance metrics. Key deliverables include:
CyberBowtie Workshops
Facilitated sessions to engage stakeholders and map out risk scenarios collaboratively.Completed CyberBowtie Worksheets
Documented models of current-state risk scenarios, threats, barriers, and consequences.Barrier Strength Scoring & Gap Analysis
Evaluation of existing safeguards to identify weaknesses and areas for improvement.Modeling of Future-State Risk Scenarios
Visualization of improved security postures based on proposed changes.Prioritized Recommendations
Actionable guidance tied to specific threats and controls, focused on reducing risk effectively.Comprehensive Report & Roadmap
A strategic document that goes beyond compliance checklists, emphasizing real-world operational impacts.
Webinar
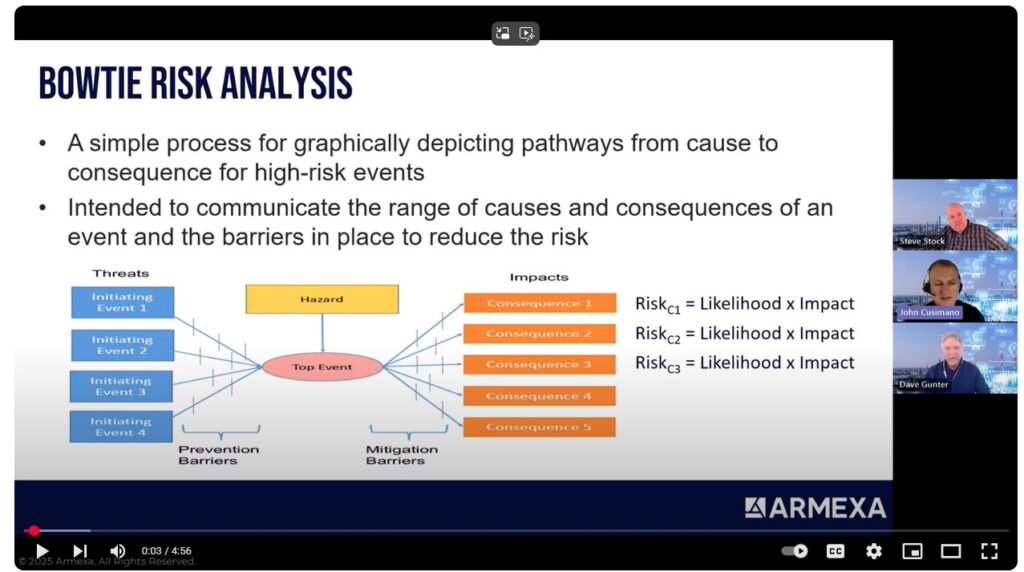
Applying Bowtie Analysis to OT Cybersecurity Risk Modeling: discusses and demonstrates through industry examples, how Bowtie Analysis has been applied to study OT cybersecurity risk and how the output of such as study can serve as the basis for the development of a site-specific cyber risk model that can be integrated with real-time data to provide a dynamic cyber risk dashboard for an industrial facility.
Armexa’s Consequence-Based Risk Assessment solutions identify the most critical operational risks within an industrial environment and prioritizes cost-effective mitigation strategies tailored to those risks.



